Service invocation overview
Introduction
Using service invocation, your application can reliably and securely communicate with other applications using the standard gRPC or HTTP protocols.
In many environments with multiple services that need to communicate with each other, developers often ask themselves the following questions:
- How do I discover and invoke methods on different services?
- How do I call other services securely with encryption and apply access control on the methods?
- How do I handle retries and transient errors?
- How do I use tracing to see a call graph with metrics to diagnose issues in production?
Dapr addresses these challenges by providing a service invocation API that acts as a combination of a reverse proxy with built-in service discovery, while leveraging built-in distributed tracing, metrics, error handling, encryption and more.
Dapr uses a sidecar architecture. To invoke an application using Dapr, you use the invoke API on any Dapr instance. The sidecar programming model encourages each applications to talk to its own instance of Dapr. The Dapr instances discover and communicate with one another.
Service invocation
The diagram below is an overview of how Dapr’s service invocation works.
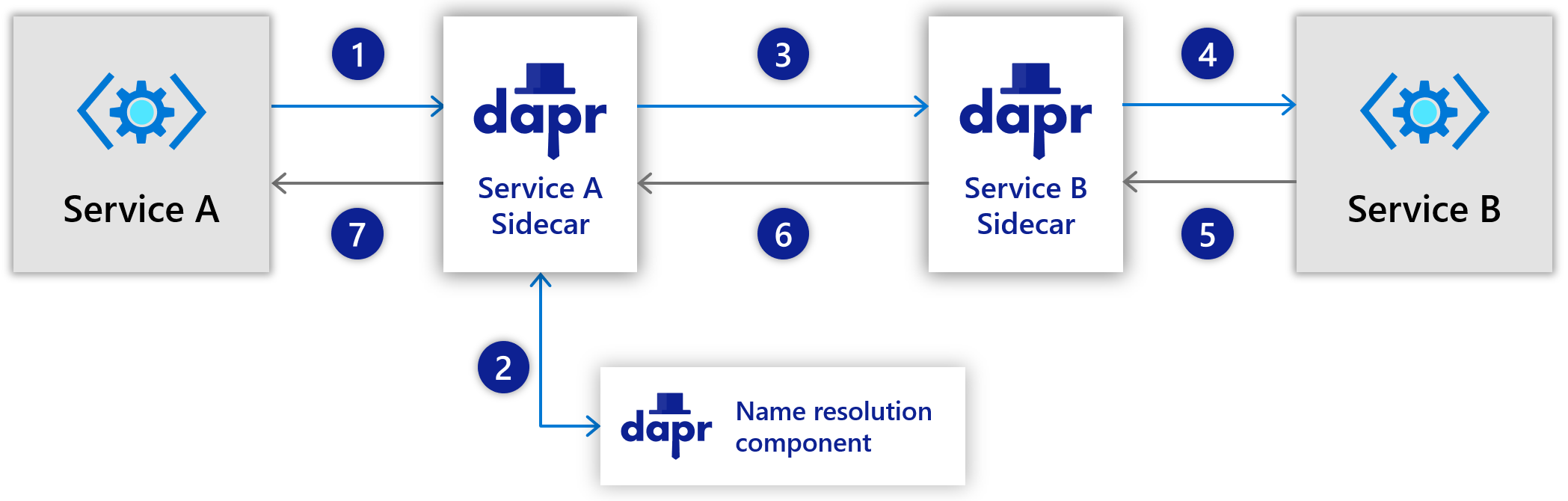
Service A makes an HTTP or gRPC call targeting Service B. The call goes to the local Dapr sidecar.
Dapr discovers Service B’s location using the name resolution component which is running on the given hosting platform.
Dapr forwards the message to Service B’s Dapr sidecar
Note: All calls between Dapr sidecars go over gRPC for performance. Only calls between services and Dapr sidecars can be either HTTP or gRPC
Service B’s Dapr sidecar forwards the request to the specified endpoint (or method) on Service B. Service B then runs its business logic code.
Service B sends a response to Service A. The response goes to Service B’s sidecar.
Dapr forwards the response to Service A’s Dapr sidecar.
Service A receives the response.
Features
Service invocation provides several features to make it easy for you to call methods between applications.
Namespaces scoping
Service invocation supports calls across namespaces. On all supported hosting platforms, Dapr app IDs conform to a valid FQDN format that includes the target namespace.
For example, the following string contains the app ID nodeapp in addition to the namespace the app runs in production.
localhost:3500/v1.0/invoke/nodeapp.production/method/neworder
This is especially useful in cross namespace calls in a Kubernetes cluster. Watch this video for a demo on how to use namespaces with service invocation.
Service-to-service security
All calls between Dapr applications can be made secure with mutual (mTLS) authentication on hosted platforms, including automatic certificate rollover, via the Dapr Sentry service. The diagram below shows this for self hosted applications.
For more information read the service-to-service security article.
Service access policies security
Applications can control which other applications are allowed to call them and what they are authorized to do via access policies. This enables you to restrict sensitive applications, that say have personnel information, from being accessed by unauthorized applications, and combined with service-to-service secure communication, provides for soft multi-tenancy deployments.
For more information read the access control allow lists for service invocation article.
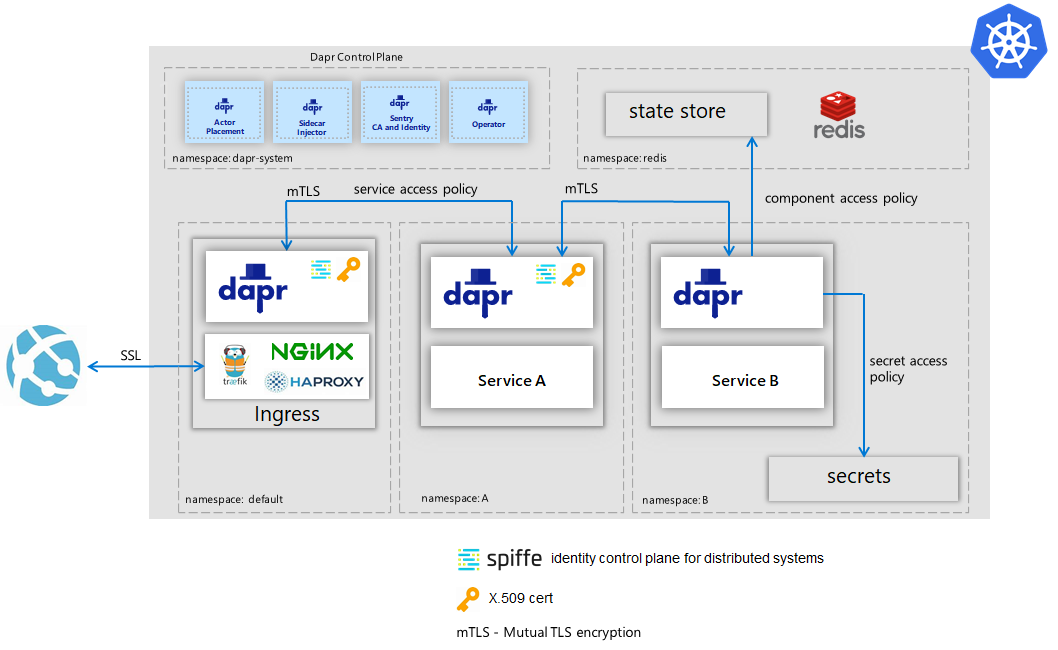
Example service invocation security
The diagram below is an example deployment on a Kubernetes cluster with a Daprized Ingress service that calls onto Service A using service invocation with mTLS encryption and an applies access control policy. Service A then calls onto Service B also using service invocation and mTLS. Each service is running in different namespaces for added isolation.
Retries
Service invocation performs automatic retries with backoff time periods in the event of call failures and transient errors.
Errors that cause retries are:
- Network errors including endpoint unavailability and refused connections.
- Authentication errors due to a renewing certificate on the calling/callee Dapr sidecars.
Per call retries are performed with a backoff interval of 1 second up to a threshold of 3 times. Connection establishment via gRPC to the target sidecar has a timeout of 5 seconds.
Pluggable service discovery
Dapr can run on any hosting platform. For the supported hosting platforms this means they have a name resolution component developed for them that enables service discovery. For example, the Kubernetes name resolution component uses the Kubernetes DNS service to resolve the location of other applications running in the cluster. For local and multiple physical machines this uses the mDNS protocol.
Note: For local and physical machines, ensure mDNS is functioning properly.
Round robin load balancing with mDNS
Dapr provides round robin load balancing of service invocation requests with the mDNS protocol, for example with a single machine or with multiple, networked, physical machines.
The diagram below shows an example of how this works. If you have 1 instance of an application with app ID FrontEnd and 3 instances of application with app ID Cart and you call from FrontEnd app to Cart app, Dapr round robins' between the 3 instances. These instance can be on the same machine or on different machines. .
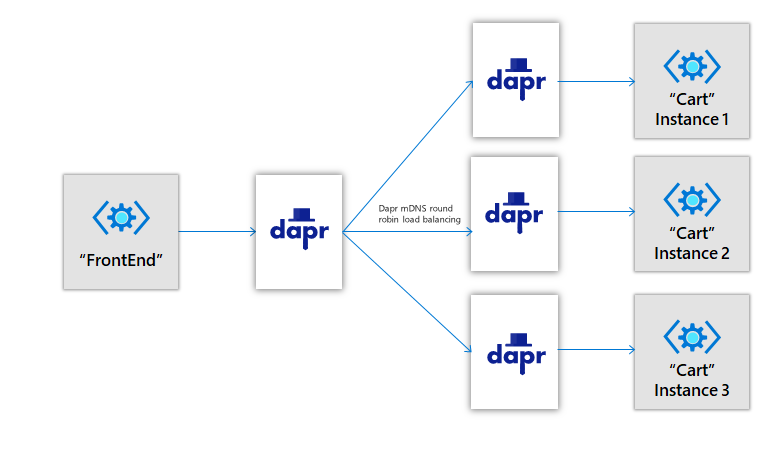
Note: You can have N instances of the same app with the same app ID as app ID is unique per app. And you can have multiple instances of that app where all those instances have the same app ID.
Tracing and metrics with observability
By default, all calls between applications are traced and metrics are gathered to provide insights and diagnostics for applications, which is especially important in production scenarios. This gives you call graphs and metrics on the calls between your services. For more information read about observability.
Service invocation API
The API for service invocation can be found in the service invocation API reference which describes how to invoke a method on another service.
Example
Following the above call sequence, suppose you have the applications as described in the hello world quickstart, where a python app invokes a node.js app. In such a scenario, the python app would be “Service A” , and a Node.js app would be “Service B”.
The diagram below shows sequence 1-7 again on a local machine showing the API calls:
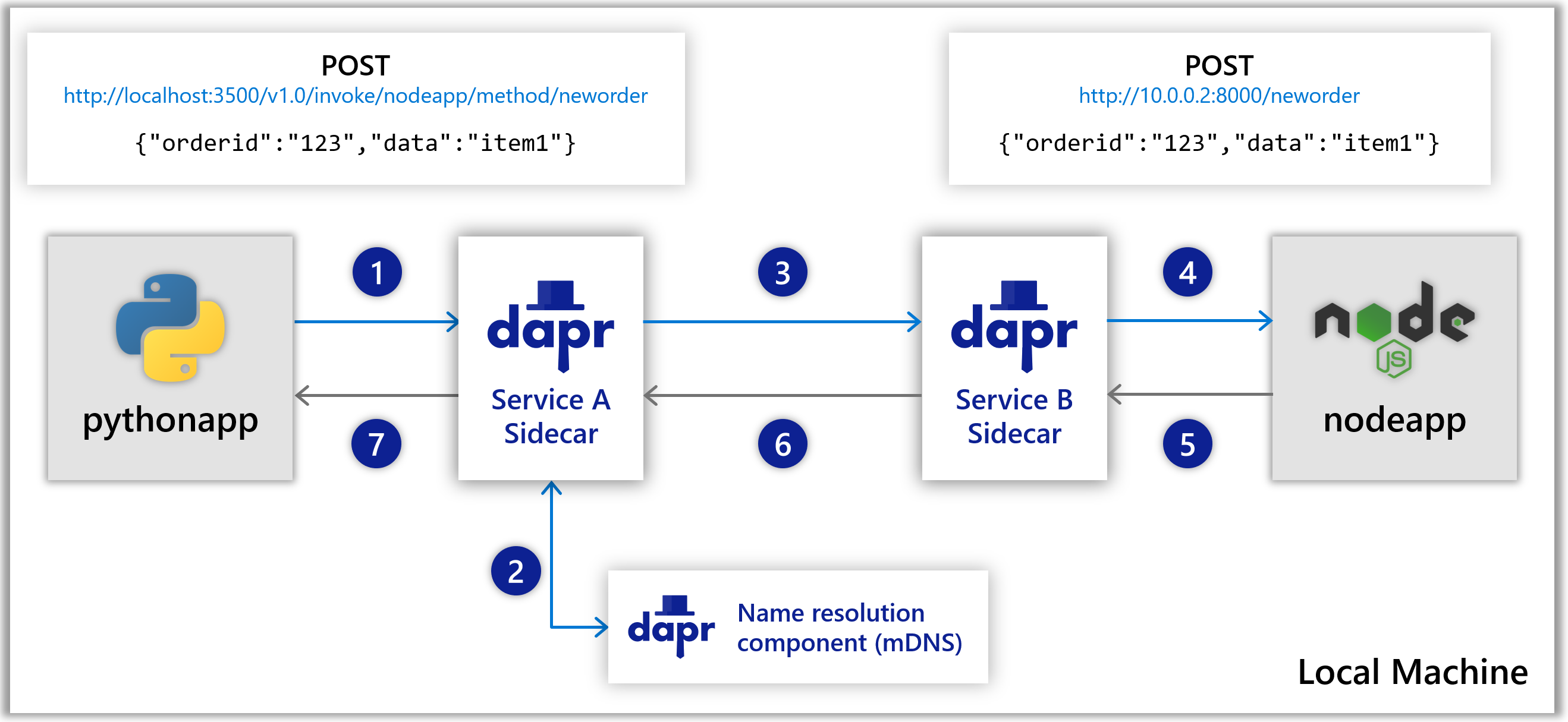
- The Node.js app has a Dapr app ID of
nodeapp. The python app invokes the Node.js app’snewordermethod by POSTinghttp://localhost:3500/v1.0/invoke/nodeapp/method/neworder, which first goes to the python app’s local Dapr sidecar. - Dapr discovers the Node.js app’s location using name resolution component (in this case mDNS while self-hosted) which runs on your local machine.
- Dapr forwards the request to the Node.js app’s sidecar using the location it just received.
- The Node.js app’s sidecar forwards the request to the Node.js app. The Node.js app performs its business logic, logging the incoming message and then persist the order ID into Redis (not shown in the diagram)
- The Node.js app sends a response to the Python app through the Node.js sidecar.
- Dapr forwards the response to the Python Dapr sidecar
- The Python app receives the response.
Next steps
- Follow these guides on:
- Try out the hello world quickstart which shows how to use HTTP service invocation or try the samples in the Dapr SDKs
- Read the service invocation API specification
- Understand the service invocation performance numbers